Did you hear about last month’s IoT hack? Regardless of when you’re reading this, it’s a legitimate question owing to the endless parade of high-profile breaches of IoT devices.
However, the IoT security situation need not be this way. Because of ongoing security issues, the United States Department of Homeland Security (DHS) in November 2016 listed six principles to address IOT security challenges [1]:
- Incorporate security at the design phase
- Advance security updates and vulnerability management
- Build on proven security practices
- Prioritize security measures according to potential impact
- Promote transparency across IoT
- Connect carefully and deliberately
A recent NXP white paper summarizes how our processors and software address each principle. A key underlying NXP technology — hardware root of trust — that supports the first two of these principles deserves further discussion.
A hardware root of trust is important because, as much as we like to think of designs as being intrinsically secure, security relies on a nested series of assumptions. An aspect of a system is considered secure on the tacit assumption that some other aspect is secure, which in turn depends on the security of yet another aspect. Hopefully, the innermost nugget depends on a set of assumptions that are highly improbable to violate.
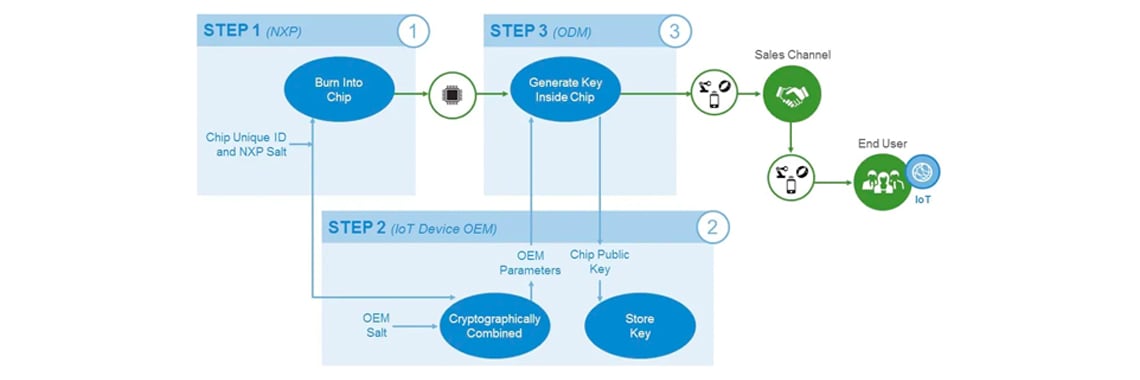
A hardware root of trust can be this nugget. Our processors generate their own device-specific private keys, unknown to even us and based on parameters supplied by our customers, to encrypt code and data. The processor chip burns these keys into itself using electrically programmed fuses. We design the chip with no circuitry that can read out the keys and add antitamper features to protect the chip from physical attack.
A hardware root of trust helps our customers incorporate security at the design phase. Secure boot, for example, is an unbypassable mechanism for developers to lock down their code. Using our tools and processors, developers cryptographically sign their software. Each time the system boots, the NXP processor validates the digital signature. Only proven authentic software can execute. Attacks that modify the system software for nefarious purposes are detected and blocked.
The same capabilities that secure the boot process can also secure the software-update process, keeping systems in the field from being tricked into accepting malicious updates. Software updates can be delivered through an encrypted tunnel using our processor’s network encryption hardware or delivered in the clear with an attached digital signature validated by our processor. Either mechanism can serve as proof that the update is trustworthy and therefore executable. The process is highly automated, reducing the potential for error, and allowing developers to focus on the content of the update.
Additional features close rollback vulnerabilities. Rollback is an attack strategy in which the attacker attempts to undo security updates by tricking a system into executing an authentic, but old and vulnerable, version of system software. NXP processors offer monotonic-counter and key-revocation features to detect de-authorized older revisions of software and block their execution.
Although the main thrust of the hardware root of trust is to address the first two principles, it also addresses other principles. Having been built into multiple generations of processors, it’s a proven technique. Conversely, forcing systems to boot hacked code and rollback attacks are proven attacks that the hardware root of trust helps to thwart. Such attacks, moreover, have tremendous impact because they take complete control of a system. Designers, therefore, should prioritize using our hardware root of trust.
Finally, our trust approach facilitates transparency. Although NXP processors have hardware-based secrets, these values aren’t chosen by NXP. Instead, the OEM programs its own values into electronically programmed fuses. The NXP processors can be trusted to protect the secrets, but NXP doesn’t know the OEM’s secrets.
Developers looking to avoid a starring role in the endless parade of IoT hacks should take advantage of our trust architecture, of which the hardware root of trust is an element. High-profile attacks will continue, but it is a lot less stressful when they happen to the other guy, the one who isn’t taking advantage NXP’s security features.
[with contributions by Geoff Waters]
1 Strategic Principles for Securing the Internet of Things