Today’s Internet of Things (IoT) is more security-focused than ever. In a growing number of ecosystems, to protect data, ensure
privacy and prevent cyberattacks, devices are required to use authentication, based on keys and certificates, when connecting to
cloud services, home networks or other devices. Also, more standards and ecosystems, such as Matter or Qi Wireless Charging,
require that the certificates used for authenticating devices are issued by trusted authorities.
Expensive Undertaking
Setting up and maintaining a manufacturing facility that supports the injection of keys and certificates into devices, as part
of what’s called device provisioning, is a major investment. It requires the installation of specialized security equipment that
can only be operated by trained employees following a clear security process, and not every device OEM has the resources to
upgrade their facilities in this way, especially if they have multiple manufacturing locations. While some device manufacturers
have already made the investment, many OEMs do not have the capability or expertise to develop and maintain their own solution.
As for specific applications, like those associated with
Matter and Qi, becoming an authorized trusted
authority is an even bigger undertaking, since it requires compliance to strict security policies and a rigorous audit process.
An Ongoing Challenge
Device provisioning is closely associated with manufacturing, since key and certificate injection takes place during production,
but issuing secure credentials isn’t a “one and done” process. IoT devices tend to be deployed for extended periods—sometimes
a decade or more—and security protocols can change, new security mechanisms may need to be put in place, and certificates may
need to be updated, re-issued or retired. Building the infrastructure to enable ongoing credential management and secure updates
adds to the cost of device provisioning, and increases the complexity of maintaining a fleet of IoT devices securely.
NXP EdgeLock 2GO
NXP is a recognized leader in IoT security and one of the few semiconductor manufacturers that not only provides comprehensive
provisioning services for a wide range of IoT use cases, but is also a fully authorized provider of certificates for Matter and
Qi. Our EdgeLock 2GO service gives device
OEMs a secure, simple and flexible way to provision and manage device credentials, over the entire lifecycle of the device, from
manufacturing to deployment and retirement.
At the point of manufacture, EdgeLock 2GO lets OEMs securely provision devices with keys and certificates, with different
configurations for different products, and is set up to safely include contract manufacturers in the process. EdgeLock 2GO can
also be used to provision devices in the field, with credentials provided at commissioning, and can be used to add, update and
revoke credentials through the device’s time in the field.
EdgeLock 2GO is secure and simple. It leverages the hardware-based root of trust to establish end-to-end protection for
provisioning OEM credentials into devices. EdgeLock 2GO is also flexible, as it allows OEMs to quickly create new configurations
for new products and to update credentials for existing products at any time. The benefit for OEMs is that they don’t need to
equip their manufacturing sites with complex security equipment, and they can maintain the security of their products through
the product’s lifecycle.
New: EdgeLock 2GO Programming Partners
To make security even easier for device OEMs, NXP has expanded the EdgeLock 2GO service to include a select group of carefully chosen partners – Arrow Electronics, Avnet Silica, EBV Elektronik, EPS Global and Future Electronics – who now offer secure provisioning services based on NXP EdgeLock 2GO.
Here's how the EdgeLock 2GO with programming partners works if you’re an OEM. You can use your EdgeLock 2GO account to configure
the credentials for your devices and to provision samples during the development phase. When you are ready for production, you
can order the parts and programming service from one of our partners. The partner provisions your parts according to the
settings in your EdgeLock 2GO account, and then ships the provisioned parts to your specified contract manufacturers.
Using EdgeLock 2GO programming partners, you get parts already programed and ready-to-use, and you benefit from the full
EdgeLock 2GO experience for updating and maintaining your devices in the field.
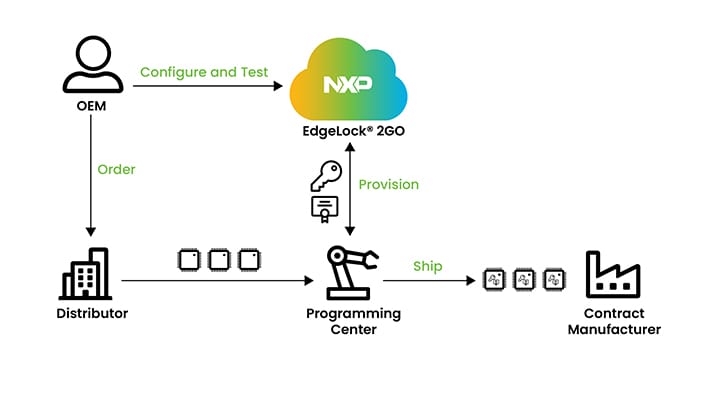 The NXP EdgeLock 2GO service with programming partners
The NXP EdgeLock 2GO service with programming partners
For better experience, download the
block diagram.
Essential to the IoT
By expanding the EdgeLock 2GO service to include partners, NXP is making it easier, simpler and more convenient for device OEMs
to provision their IoT devices. It’s part of our dedication to secure operation in the IoT, and our commitment to delivering the
services that our customers need.
The importance of device provisioning can’t be overstated. High-level security is relevant to just about every IoT use case, and
the techniques used in device provisioning are recognized as best practices for device protection.
Join the EdgeLock 2GO Managed Service. For a free trial,
sign up today.
The IoT is, at its heart, about collecting, processing and sharing data. The operating model relies on data being authentic,
from known devices, which means devices need to support an authentication process that confirms their identity and permission to
access the network. Having a trusted device identity ensures that a device is known and legitimate, and many IoT deployments
verify identities before granting access to services or processing data. Also, because every device is a potential entry point
for unauthorized access, and because hackers never stop trying to find new ways to mount an attack, protecting device identity
is an essential and ongoing task, starting at the point of manufacturing and going through the device’s entire time in the
field.
Here are just a few examples that demonstrate how provisioning devices securely is an essential part of enabling IoT use cases:
- Data protection and privacy
The IoT serves to transmit, process and store data, and each transaction needs to be kept safe from unauthorized access,
tampering and theft. Passwords, data encryption and key management are vital to operation.
- Secure cloud onboarding
The world’s most widely used public cloud providers, including AWS and Azure, authenticate IoT devices based on keys and
certificates, as do many other private or closed infrastructures.
- Smarter, safer smart homes
Matter, the interoperability standard defined and maintained by the Connectivity Standards Alliance (CSA), is ushering in a
new era for the Smart Home segment, by making it easier for devices to communicate with each other and laying the groundwork
for safer, more automated living environments. Matter is designed to be secure, and is supported by a verification program
that requires all Matter-certified devices to follow a strict set of security and privacy principles.
- Safe wireless charging
The latest versions of the Qi specification, issued by the Wireless Power Consortium (WPC), support multiple power profiles.
Authentication is used to ensure that smartphones and other devices can accept higher energy output without risking the safety
of the device user. To pass certification, Qi devices that support the Extended Power Profile must use a tamper-resistant
subsystem that protects the private key and certificate used for authentication.
- Secure access control
A number of IoT use cases involve providing access to secure locations, whether in the physical world or online. Whether
devices are used to protect access to a manufacturing facility, a conference room, a student dorm, a hotel room, your front
door or a protected online service, keys and credentials are used to operate the rules for access control.
- Safe software updates
When devices need to be updated in the field, secure mechanisms for maintaining verification and decryption keys, with secure
connections to dedicated update services, make it possible for already-deployed devices to keep up with changing security
requirements.
Take the Next Step
Visit our EdgeLock 2GO, page to explore the many ways device OEMs can benefit from the provisioning service offered by NXP and our partners.


