Presented by
-
Distinguished Engineer and Managing Director, Microsoft
Sign in for a personalized NXP experience.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.

This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
This is a modal window.
Beginning of dialog window. Escape will cancel and close the window.
End of dialog window.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
This is a modal window. This modal can be closed by pressing the Escape key or activating the close button.
Sign in to access this content and additional site features. Don’t have an account? Register now.
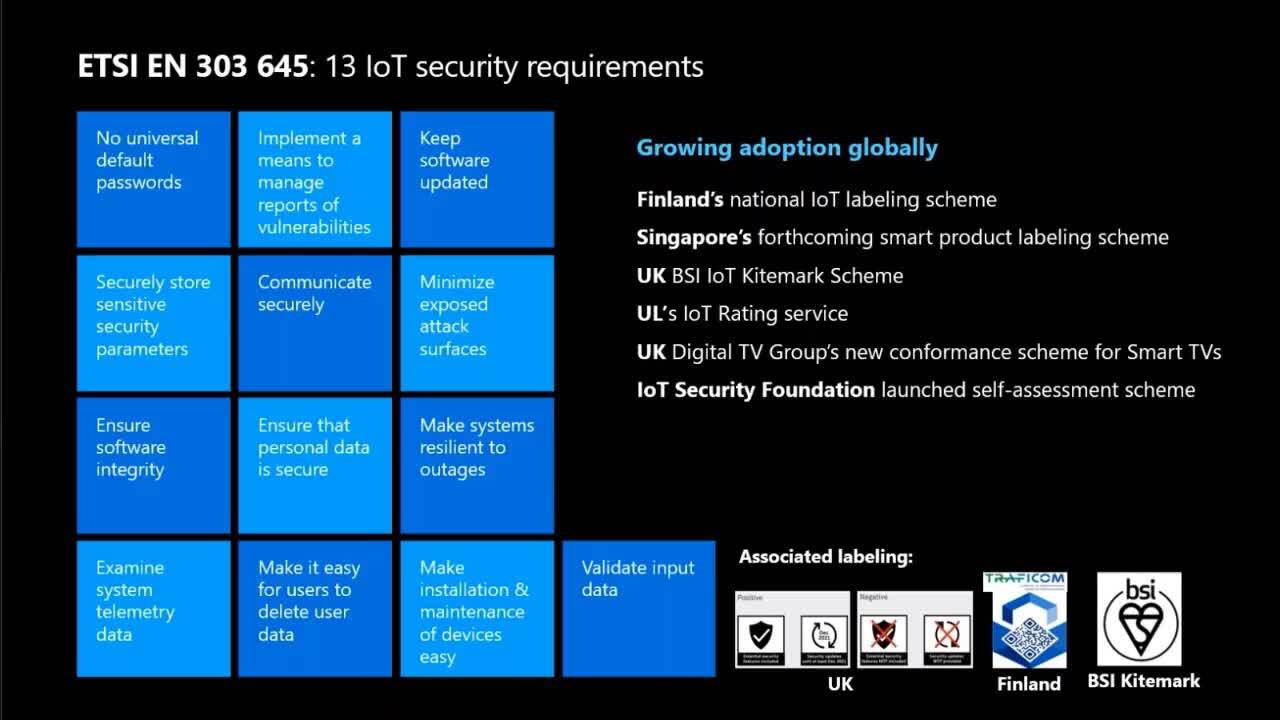
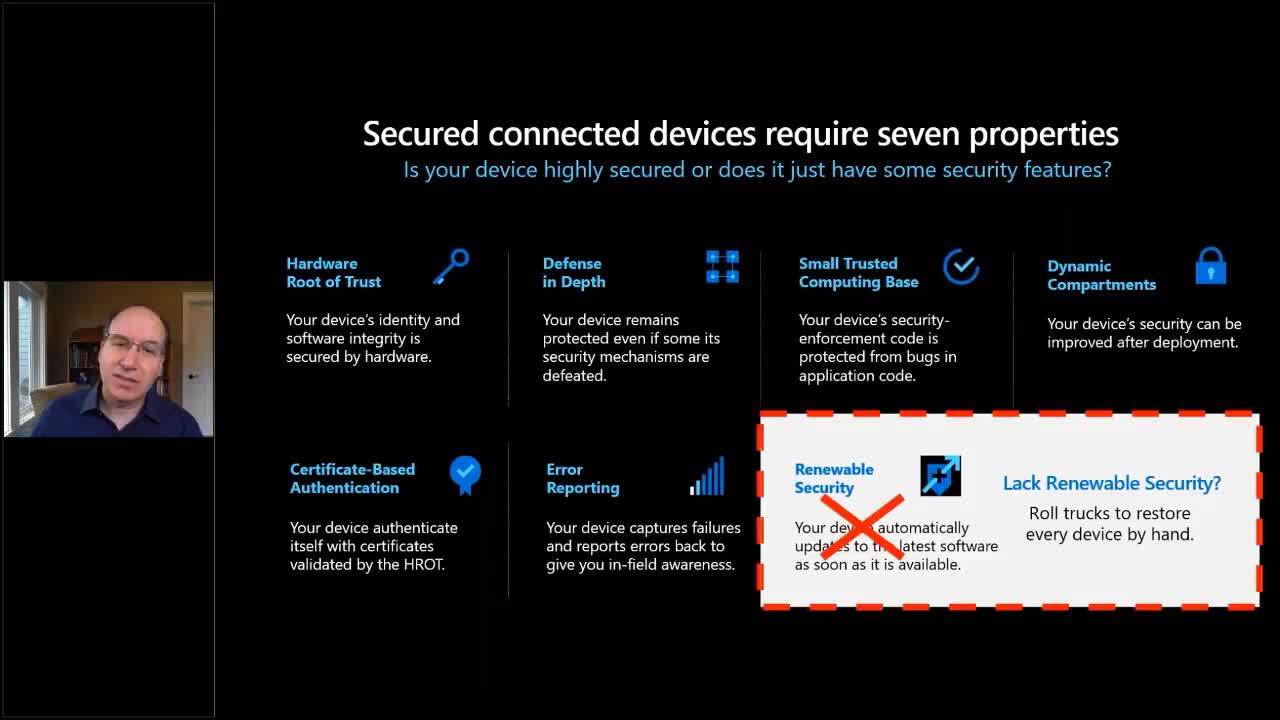
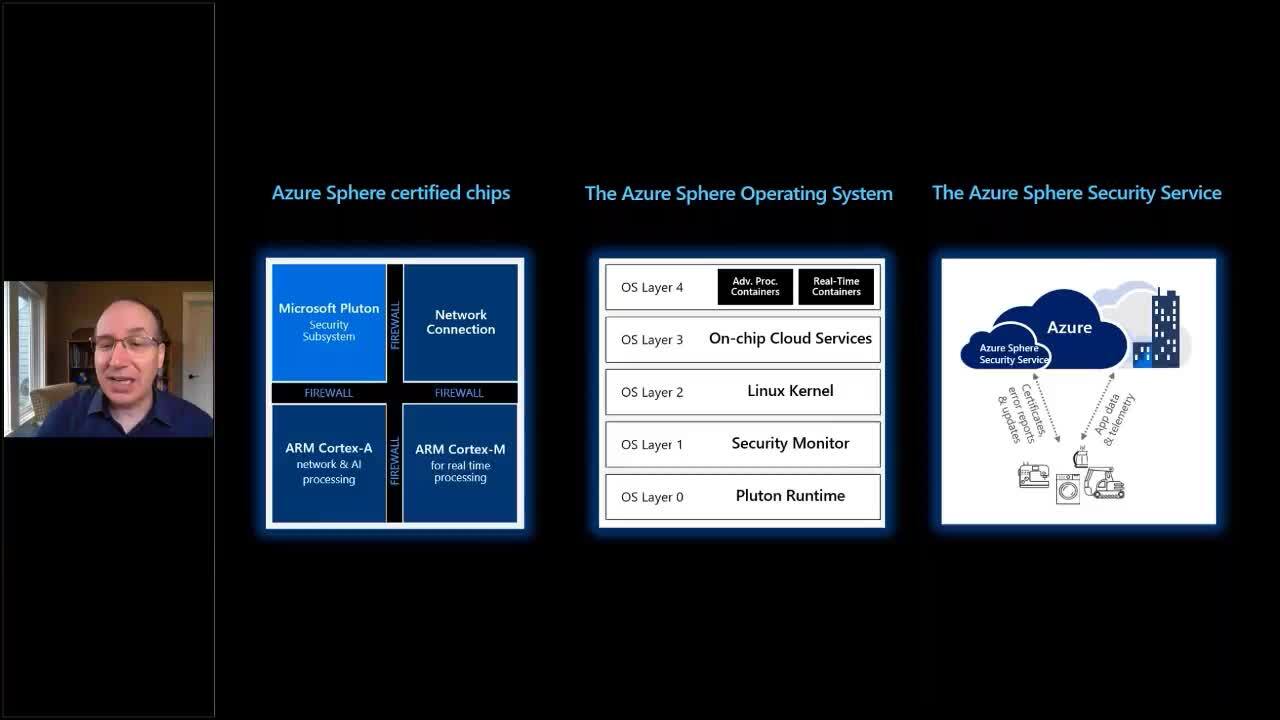
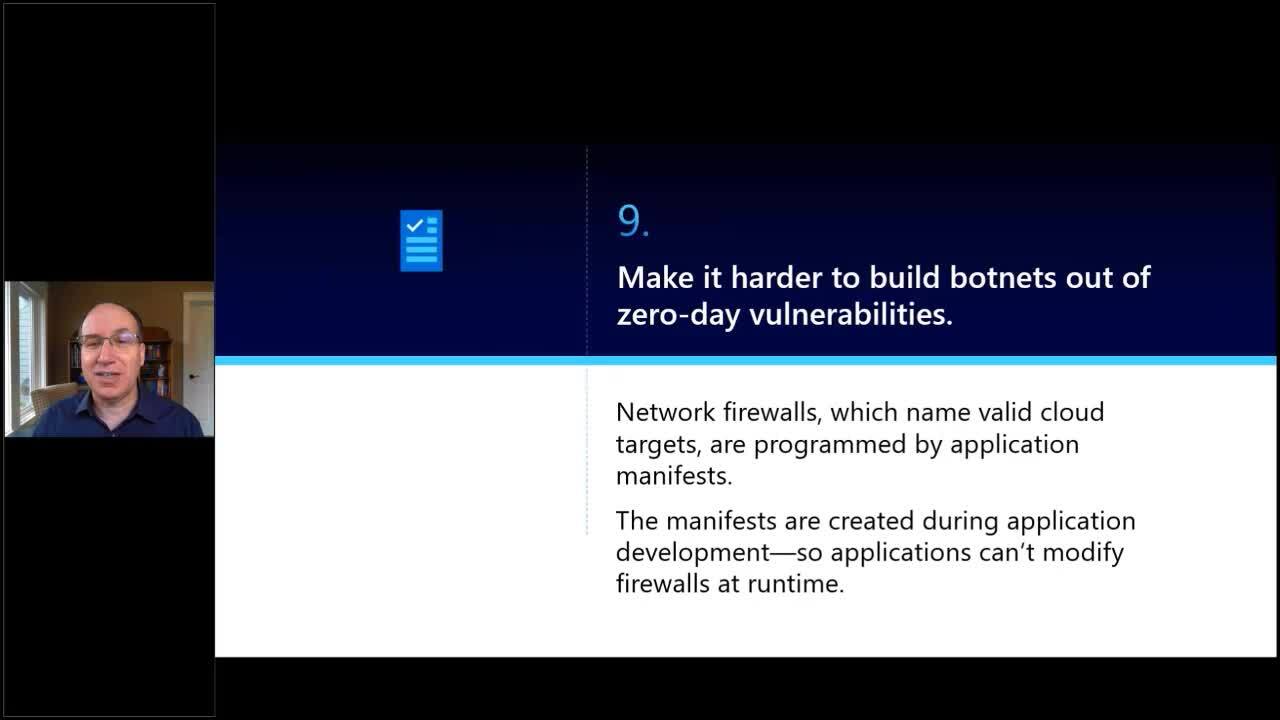
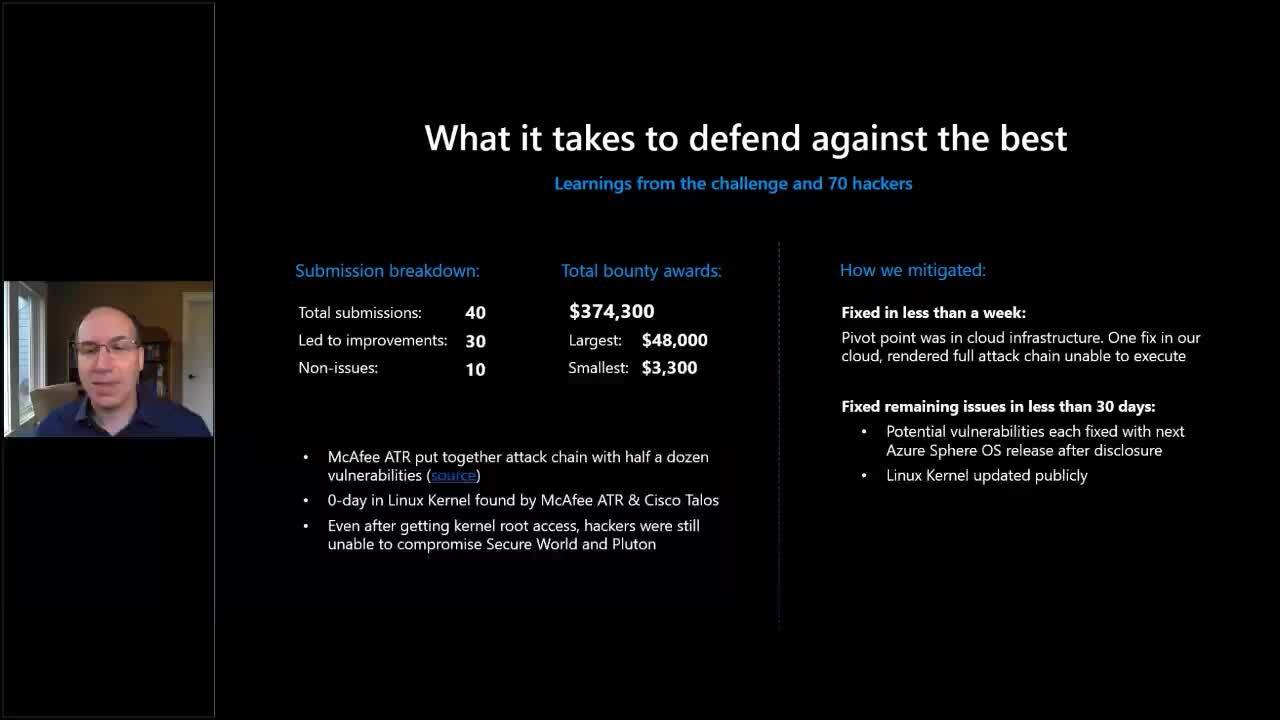
IoT investments can transform business operations, increase telemetry and improve safety. However, without a clear understanding of the unique cyberthreat landscape, IoT introduces tremendous risk. Securing connected devices is not a simple task – it requires significant upfront investments in security before an IoT product even launches. Nevertheless, putting a device in the hands of the customer is only the beginning of an ongoing battle with the real-world threat landscape. In this session, we’ll share foundational knowledge about what it takes to secure connected devices over time and learnings from our experience inviting 70 of the worlds most determined hackers to attack our product.
Subscribe to our newsletter to stay updated with our latest developments and if you need further assistance, we are here to help.
Subscribe Contact Support
Help us improve your experience on our site. We invite you to take our five-question survey.